Firewalling Examples with Security Groups
Understanding ICMP
On top of TCP and UDP traffic, the internet Protocol (IP) can also carry ICMP messages.
While all ICMP requests are closed by default on your instances, it is easy to add the ECHO REPLY ICMP traffic rule to your security group so you can ping your instance. With ping activated to an instance, it is easier to enable it in your preferred monitoring tool or service.
Adding Ping to Your Instances
To add ingress ping connectivity to your instance:
-
Choose the Security Group: Navigate to the instance list in the Portal and choose the security group enabled on your instance that you want to add ping traffic to. Please note that all instances belonging attached to this security group will gain ping access as well.
-
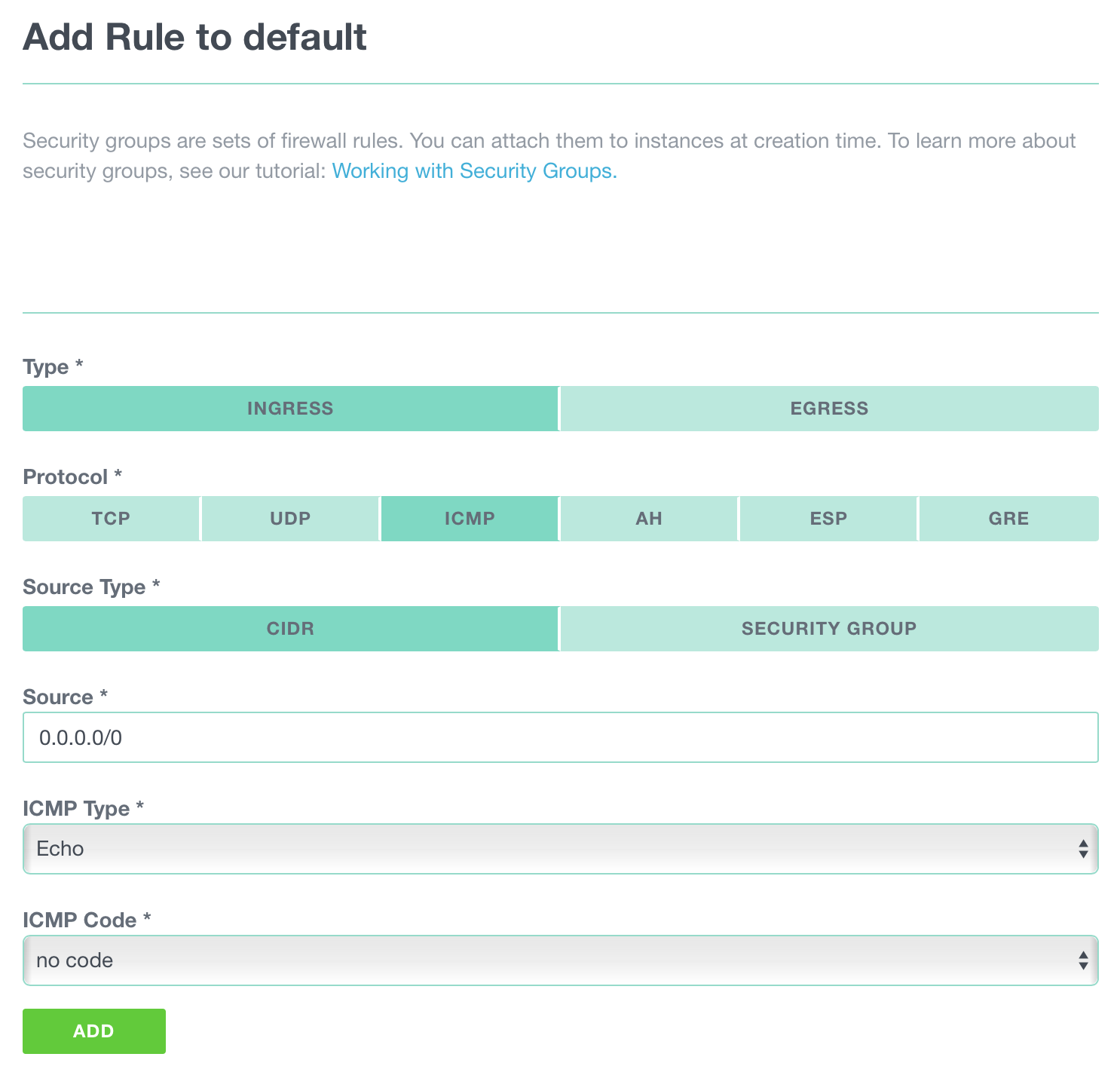
Add a rule: In the selected security group, add an
INGRESSrule, restrict the source IP or network range, then select the ICMP protocol. -
Echo: Select the type ECHO (type 8) and code NO CODE.
-
Save: Click on ADD to save your rule. Allow a few moments for the rule to propagate.
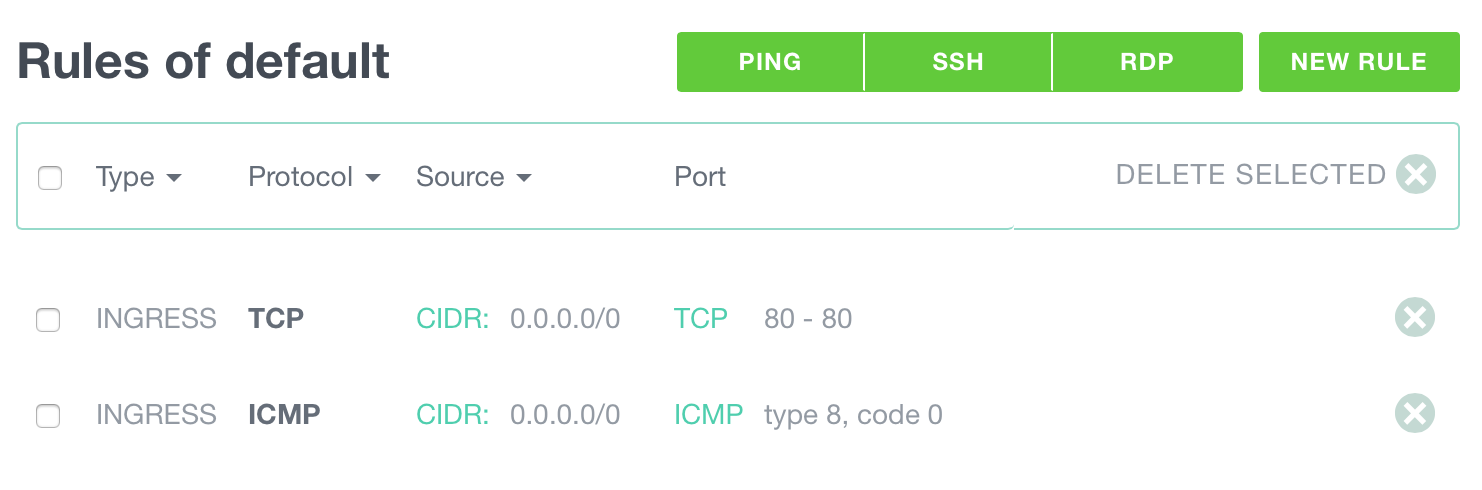
The resulting rules appear like this:
Reminder
-
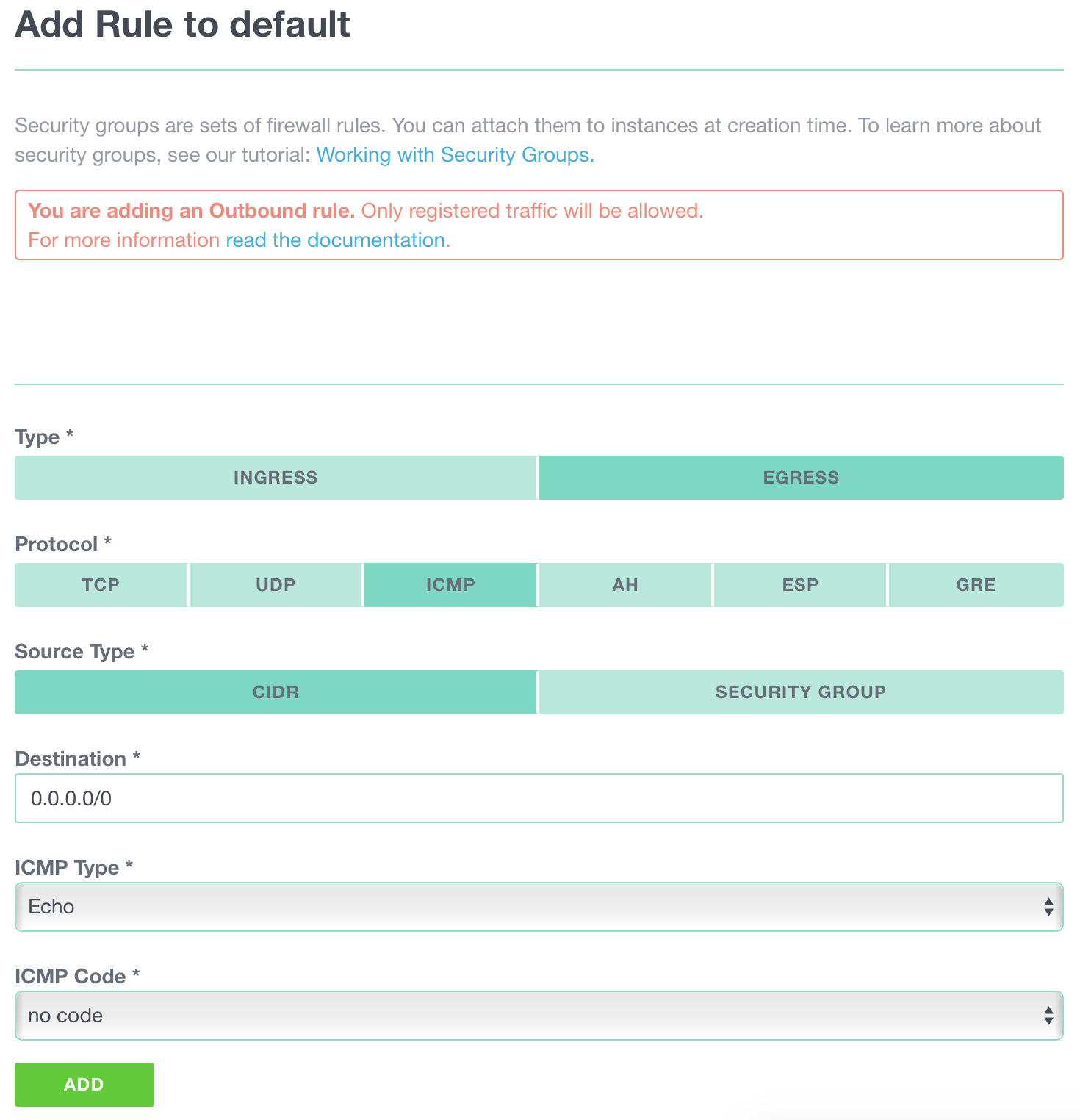
Outbound traffic: By default, all outbound traffic is permitted. However, as soon as you define an outbound rule outbound traffic is only allowed for the defined outbound rules. See managing outbound security rules for more information.
-
Allow Outbound Reply: To allow outbound reply if the outbound traffic is restricted, add an outbound rule with ICMP Type ECHO REPLY (type 0) and code NO CODE.
Allowing HTTP and HTTPS Access to Your Instance
When you deploy an application on your server, you might want it accessible via a browser, either via HTTP or HTTPS. To do that, you need ingress rules in a security group to allow communication on port 80 (HTTP) and 443 (HTTPS).
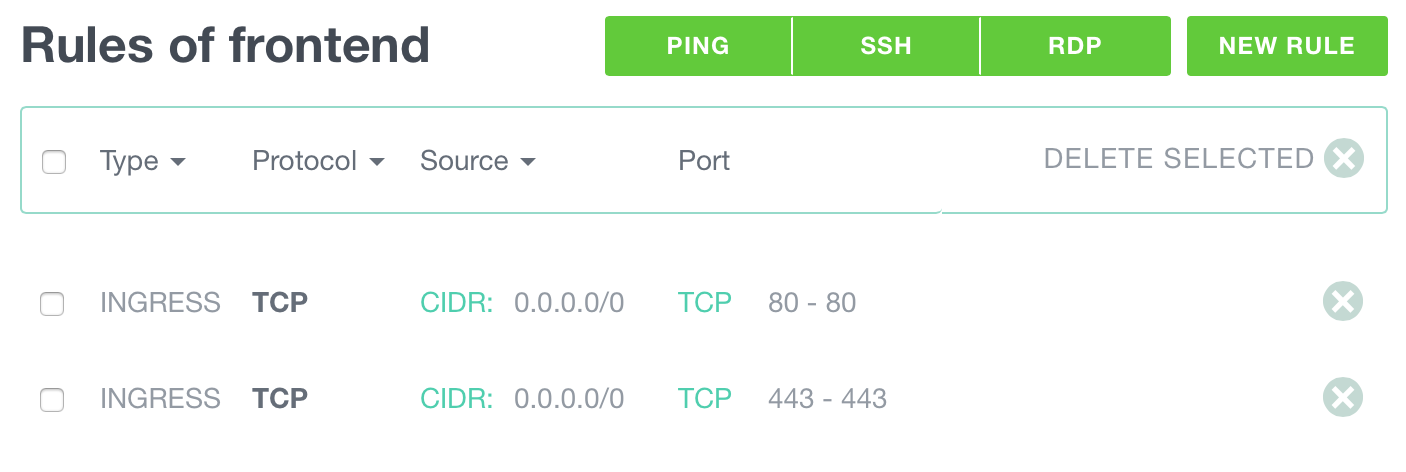
- Create a new security group called frontend
- Add a first rule:
INGRESS, TCP, CIDR 0.0.0.0/0, port 80-80 - Add another rule: ingress, TCP, CIDR 0.0.0.0/0, port 443-443
Now the instances using this security group will allow traffic from any IP (CIDR 0.0.0.0/0) on port 80 and 443.
Add this Security Group to the instance that will be accessed via HTTP and HTTPS.
If your instance only has this Security Group, you will not be able to access it via SSH.
Allowing SSH Access to Your Instance
After an instance is deployed, if you want to manage it via SSH, you should allow incoming traffic on port 22.
However, we recommend that you create a Security Group dedicated to the management of your machines. If you add some granularity in your security groups, will make work easier when you have more complex setups.
- Create a new security group called management.
- Add a new rule:
INGRESS, TCP, port 22. - Change the CIDR for this rule to your IP range. You don’t want to allow every IP to be able to connect to your machine via SSH.
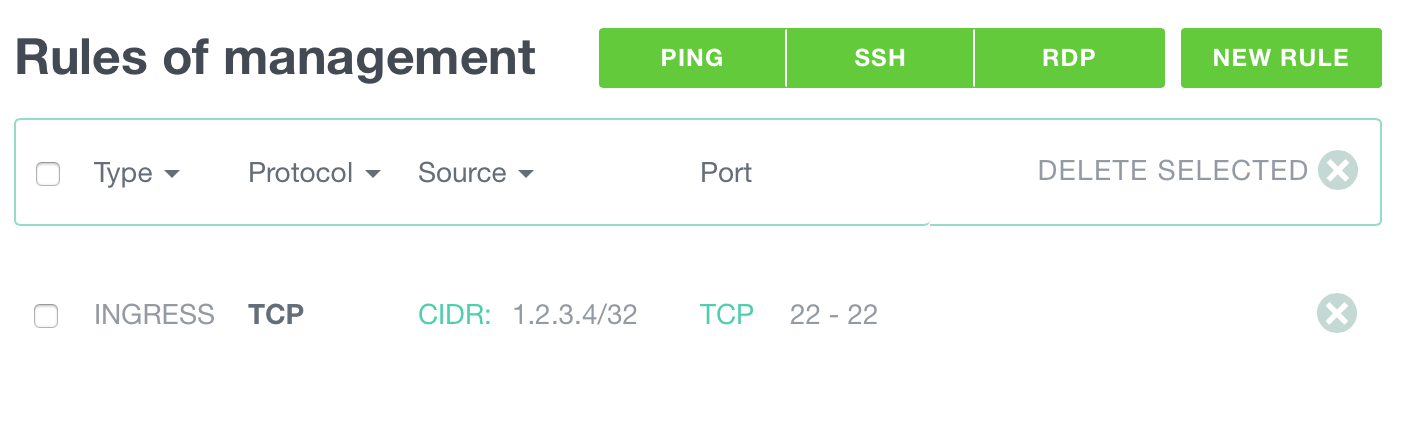
Add this security group to the instances you want to manage via SSH.
