Single Sign-On Authentication
Allow single sign-on for users on an Exoscale account using an Open ID Connect, also known as OIDC. identity provider. SSO organization connect for Exoscale is available from our Starter support plan level and up.
Activation
Accessible to users with OWNER user role in the IAM section of the main navigation, under SSO.
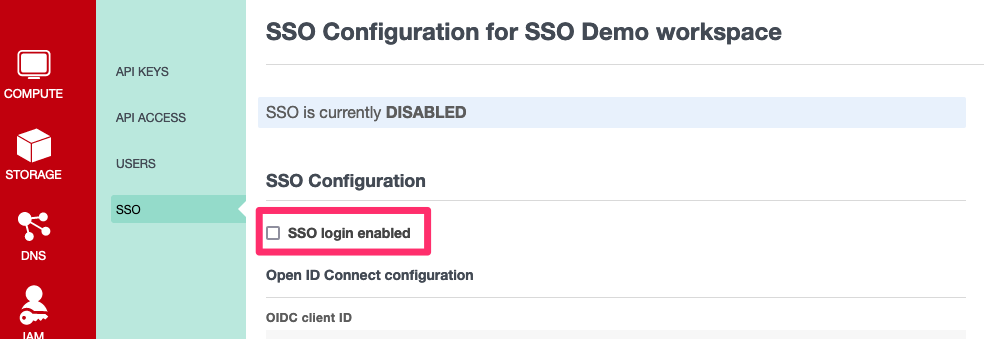
Configuration
Accessible to users with OWNER user role in the IAM section of the main navigation, under SSO.
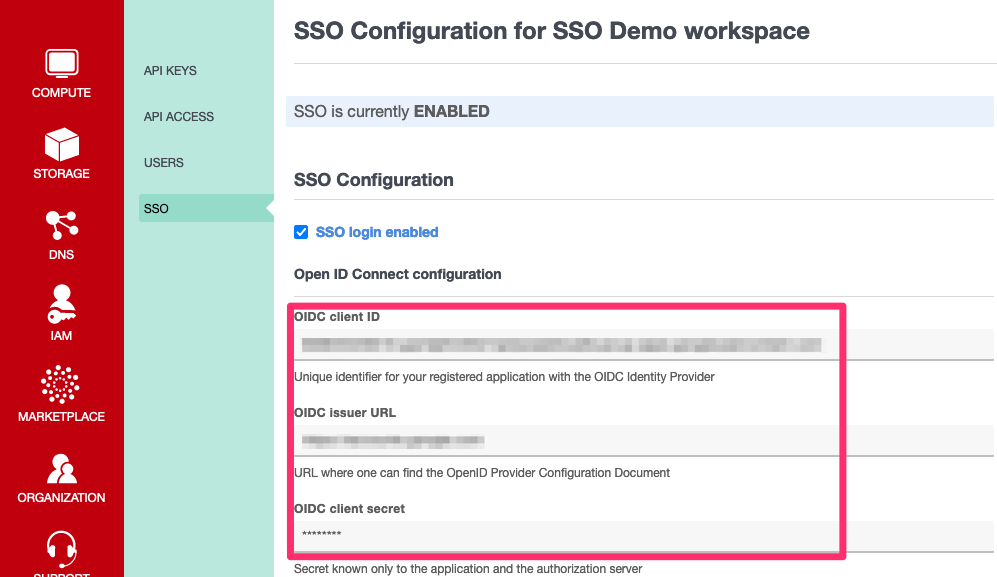
You need to enter:
- your OIDC
Client ID - the OIDC
Issuer URL - your OIDC
Client Secret
This is the URL you need to authorize on the OIDC provider side: https://portal.exoscale.com/sso-authenticate/<sso-org-name>
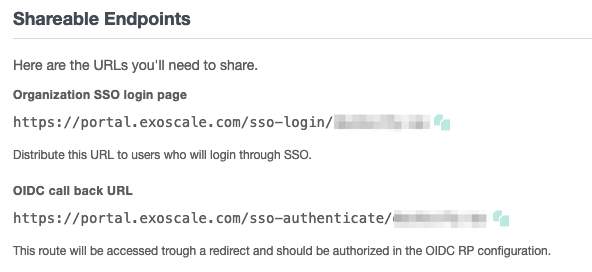
Login
The URL for the SSO login page: https://portal.exoscale.com/sso-login/<sso-org-name>

When a user logs in an organization using SSO, a new, unique user is created inside this organization with the TECH role.
The username is a universally unique identifier (or UUID) to allow for a standard non-SSO user with the same email address.
Authorization
You can authorize in two ways:
- Use an ID token introspection with a Common Expression Language (or CEL) query.
- Set up your own proxy with a DEX server or equivalent.
Authorization with ID token introspection
Enter two values to perform ID token payload introspection to authorize a user:
OIDC Additional Claimswhich contains claim names (space separated)- a
Common Expression Language Authorization Expressionwhich is evaluated at login time against the ID token payload.
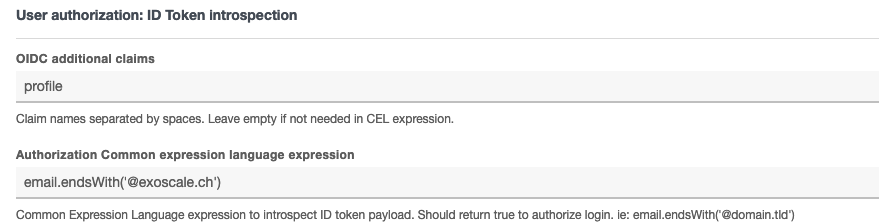
OIDC additional claims
The standard claims which are always part of the ID token payload are:
openidprofileemail
If you need to introspect additional claims, you need to enter them in the OIDC Additional Claims field.
Common Expression Language Authorization Expression
This Common Expression Language query will be evaluated at login time against the ID token payload.
If the CEL authorization expression evaluation returns true, the user can log in.
With all other return values, the user cannot log in.